

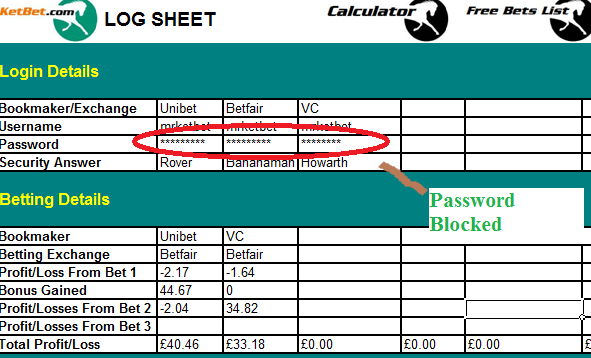
Top: An example of searching of excel file with username and password inputs.
Secondly, instead of the old search we now use "index.of passlist" to look for clear text files, the question asked me if i can figure the password. Honestly, i couldn't, what i find is only users name and folders. Maybe the password and user is both encrypted and cannot be view by normal users.
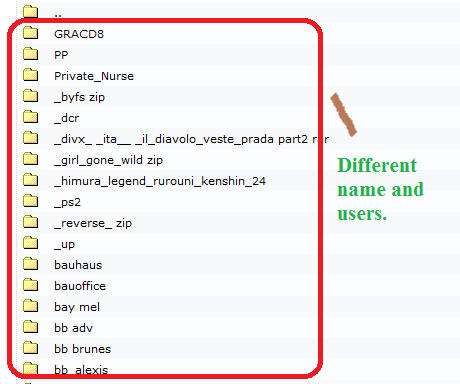
Top: Folders inside the parent folder. Different name of users/groups being found
Basically, in this practical i have learnt how attackers operate when they are looking for private information to attack people. Understanding how the attackers find it's resource, can help us prevent them from this section. Protecting a computer, is like protecting a country, understanding your enemy can help in alot of different way. In the way to information technology, understanding how an attacker work can help us prevent unwanted damage.
P1062344 posted during Tuesday, May 11, 2010 at 4:22 AM
About Me
Name: Maverick Yong Kim Wee
Chinese Name: 杨 金 辉
Admin No: P1062344
Class: DISM 1A/01
No.of readers
Comments